CrossVillage is a side event of CrossCTF 2018 where we invited three speakers to give talks on 17th June 2018. More details on the talks can be found below.
Overview
Anyone is welcomed to register for CrossVillage. You can register here: https://goo.gl/forms/20k5mPlGrlH9eBU03
Here are a list of the topics for the talks. More information can be found below.
- E2EE Fuzzing for Mobile Applications
- Introduction to Lockpicking
- Mobile App Analysis
| Information | |
| Date/Time: | 17th June 2018, 9am - 4.30pm |
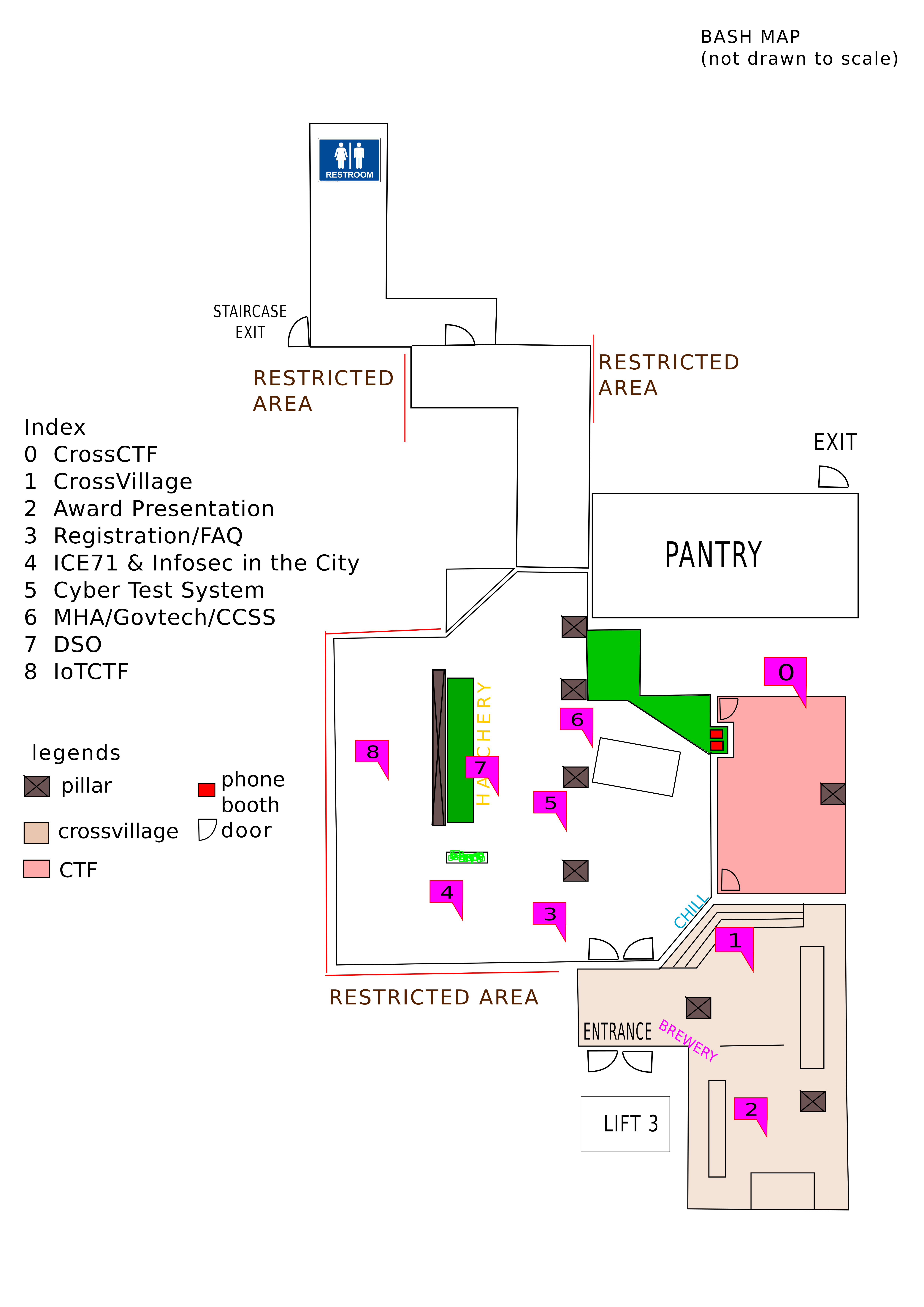
| Location: | #03-01, 79 Ayer Rajah Crescent, Singapore 139955 (Please take LIFT 3 to go up) SgInnovate’s BASH @ One-north |
There will be attractive prizes to be won from the lucky draw at the end of CrossVillage.
Pizzas will be provided for lunch and below is the schedule for CrossVillage on the day.
| Time | Event |
| 9:00am | Registration/Sign in |
| 10:00am | Talk 1 |
| 11:00am | Talk 2 |
| 12:00pm | Break for lunch |
| 1:30pm | Mid-day keynote speech |
| 2:00pm | Talk 3 |
| 3:00pm | Closing keynote speech |
| 3:30pm | Award Ceremony for Crossctf 2018 / Lucky draw ceremony |
| 4:30pm | End of event/Tea break/Networking |
Here are a list of the topics for the talks. More information can be found below.
- E2EE Fuzzing for Mobile Applications
- Introduction to Lockpicking
- Mobile App Analysis
Talk 1: E2EE Fuzzing for Mobile Applications
| Speaker Name: |
Sayed Hamzah |
| Speaker Bio: | Currently working as a Security Consultant in Centurion Information Security, Hamzah has a vast amount experience in the areas of penetration testing for mobile/web applications and enterprise network infrastructures. His skillset is further complimented with his acquisition of Offensive Security certifications (OSCP, OSCE) and CREST Registered Tester (CRT) certifications. In addition, Hamzah has been actively involved in the establishment of the Offensive Cyber Security Club in Nanyang Technological University, providing training for club members who have a keen interest in vulnerability assessment and penetration testing as a career in the future. |
| Company: |  |
| Description: | End-to-end encryption, or E2EE in short, involves encrypting data on the mobile application before it gets sent to the application server. This is mainly to prevent any attackers to tamper or inject malicious payloads while the data is in transit, in the event of a man-in-the-middle attack. However, that does not mean that the application server is safe from such attacks even if E2EE is implemented. |
Talk 2: Introduction to Lockpicking
| Speaker Name: |
Fazli Sapuan |
| Speaker Bio: | Locksmiths hate him. Check out this one weird trick he once saw someone on YouTube use to defeat a lock 9 out of 10 experts thought was adequately secure. |
| Company: | N/A |
| Description: | Physical locks are an important aspect of operations security that is often overlooked. In order to properly assess the amount of security a particular lock would provide, it would be helpful to learn its mechanism and the tried and tested methods of defeating them. (Or, you know, just just pick up the skill for fun) |
Talk 3: Mobile App Analysis
| Speaker Name: |
Tan Shu Ren |
| Speaker Bio: | Shu Ren had been working at CSIT for the past 4 years as a mobile researcher. His area of work includes investigating threats on mobile OS, performing security assessments on mobile app through code audit and reverse engineering as well as to profile and evaluate security of mobile devices. Prior to joining CSIT, Shu Ren studied Computer Science in USA, and work at Oracle Corporation for a while. |
| Company: |  |
| Description: | This year marks the 10 years in which Apple App Store and Google Play Store have been in business. Downloading, installing and using of mobile applications from these stores have become an integral part of our daily interactions with our mobile devices. However, do the users (us) really know what these mobile app offered us? Does the mobile app only offer the features that are stated upfront or are there any hidden "features" that the users (us) do not know about? |
